The Art Of Zendesk Hijacking
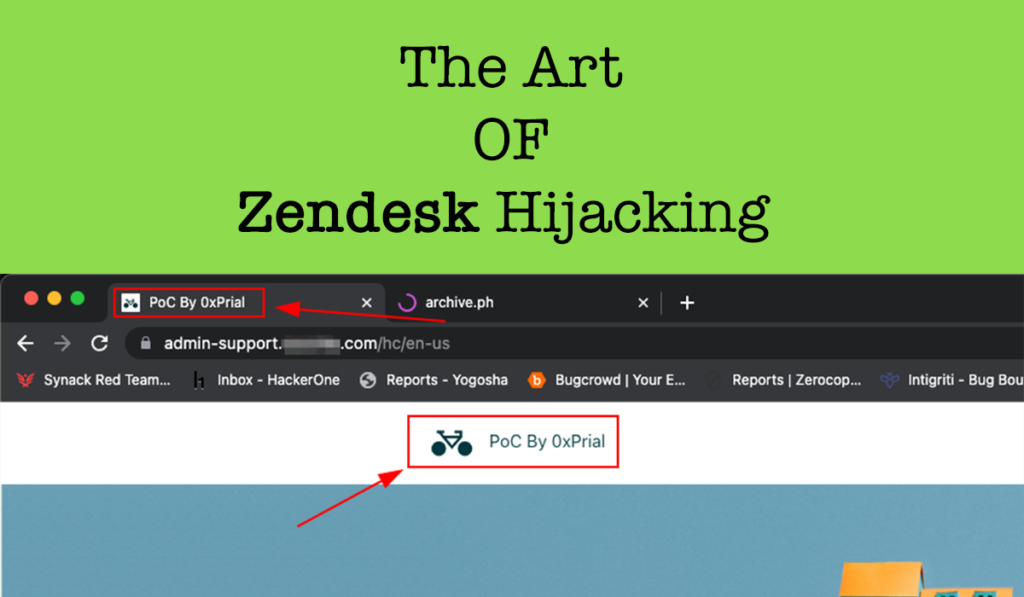
Back in July 2023, I was testing a HackerOne Private Program [ let’s call this target xyz.com ] and this target scope was pretty limited. The scope was – xyz.com admin.xyz.com api.xyz.com The subdomain admin.xyz.com looks interesting and I quickly used search.censys.io to look for any beta or dev environment for this admin subdomain using the query […]
Subdomain Hijacking Of Any Qwilr’s Customer

First Happy new year to fellow Hackers, I was planning to write on my blog regularly for the last few months, but I could not do that due to my lack of time and laziness. So here’s a new year gift for you guys ? Back in October 2022, I was testing a really old […]
IDOR Leads To Leak Any Uber Eats Restaurant Analytics
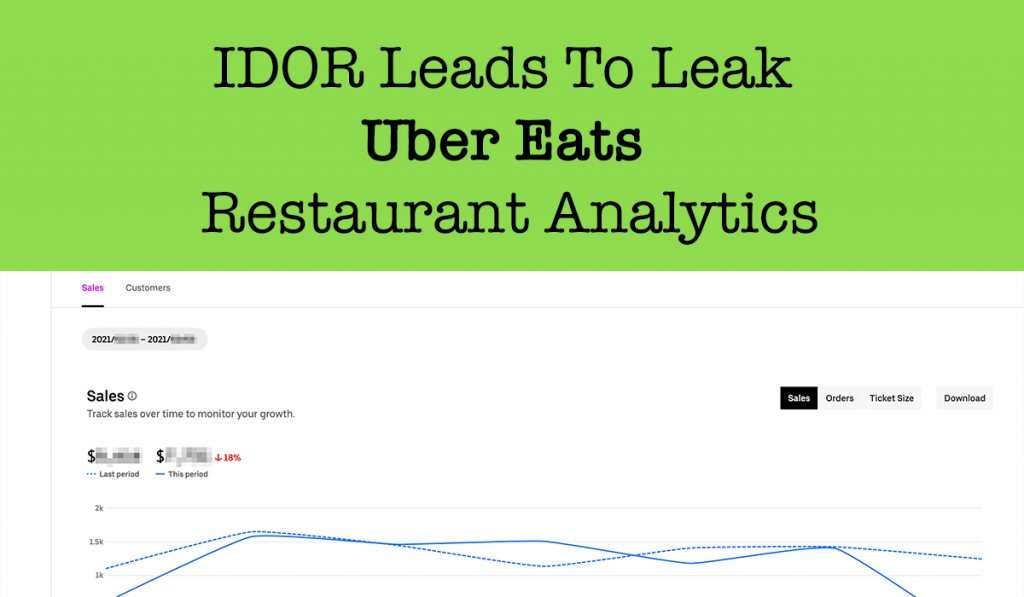
Hi fellow Hackers,At first Ramadan Kareem! Wishing everyone a very happy Ramadan. Today I will write about an Insecure direct object references (IDOR) vulnerability that I recently discovered in Uber Eats Restaurant. The Uber Eats Restaurant web application at https://restaurant.uber.com/ is using GraphQL. Back in March, I was doing a collaboration on a Uber report […]
XSS WAF & Character limitation bypass like a boss
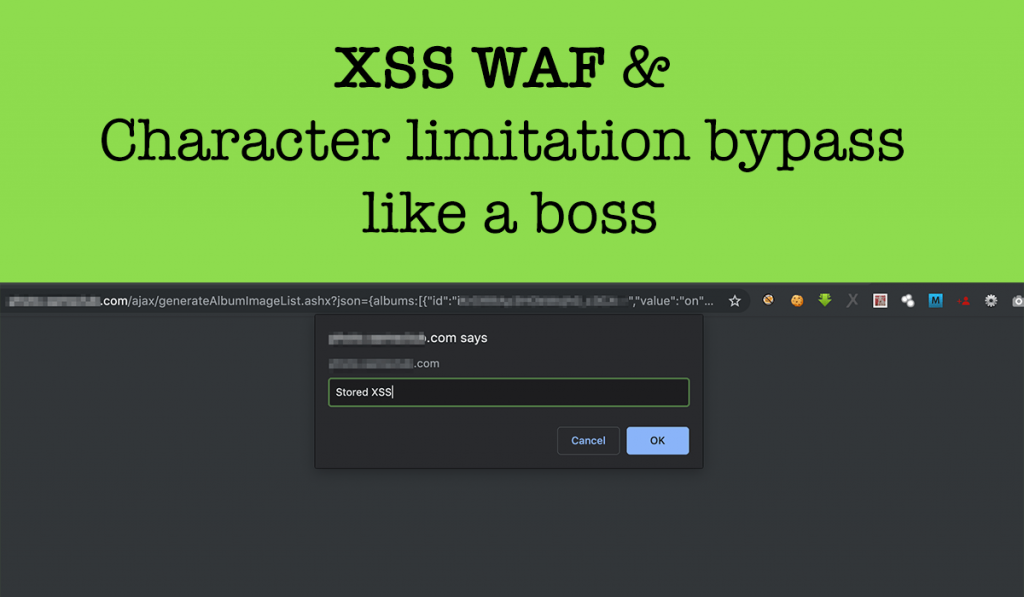
Hello fellow Hackers! I am sitting in my room for the last 3 days due to the coronavirus outbreak worldwide and feeling really bored. So I thought why not do a write-up of what I promised really long ago 🤭. A few months back in My Tweet I shared a way to bypass XSS WAF […]
Unicode vs WAF — XSS WAF Bypass
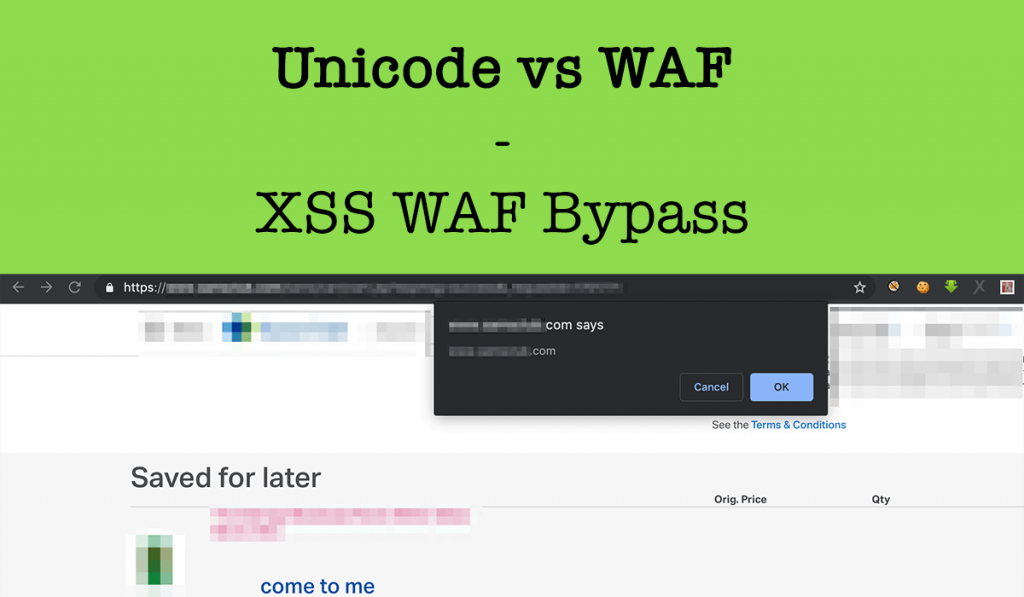
Hi readers, At 1st Eid Mubarak to all. May Allah bring you joy, happiness, peace, and prosperity on this blessed occasion. Wishing you and your family on this happy occasion of Eid! Eid Mubarak! So on this blessed occasion I thought let’s share one of my findings as an Eid bonus 😜 ! From the […]
XSS bypass using META tag in realestate.postnl.nl
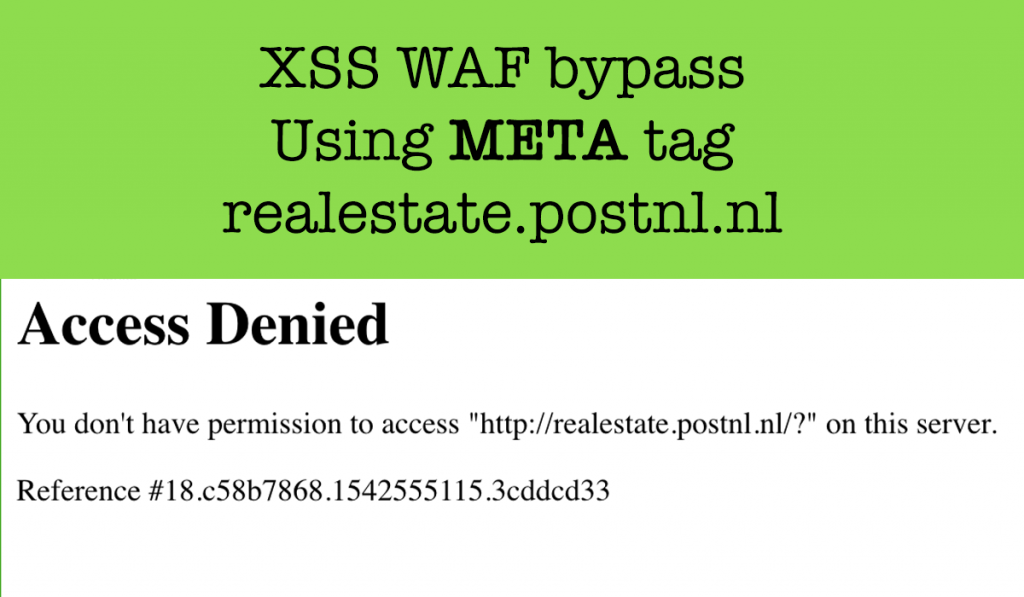
Hi readers, Today I will write about a XSS Vulnerability I reported to the postnl.nl bug bounty Program. Reflected XSS A reflected XSS (or also called a non-persistent XSS attack) is a specific type of XSS whose malicious script bounces off of another website to the victim’s browser. It is passed in the query, typically, […]
How I earned 5040$ from Twitter by showing a way to Harvest other users IP address
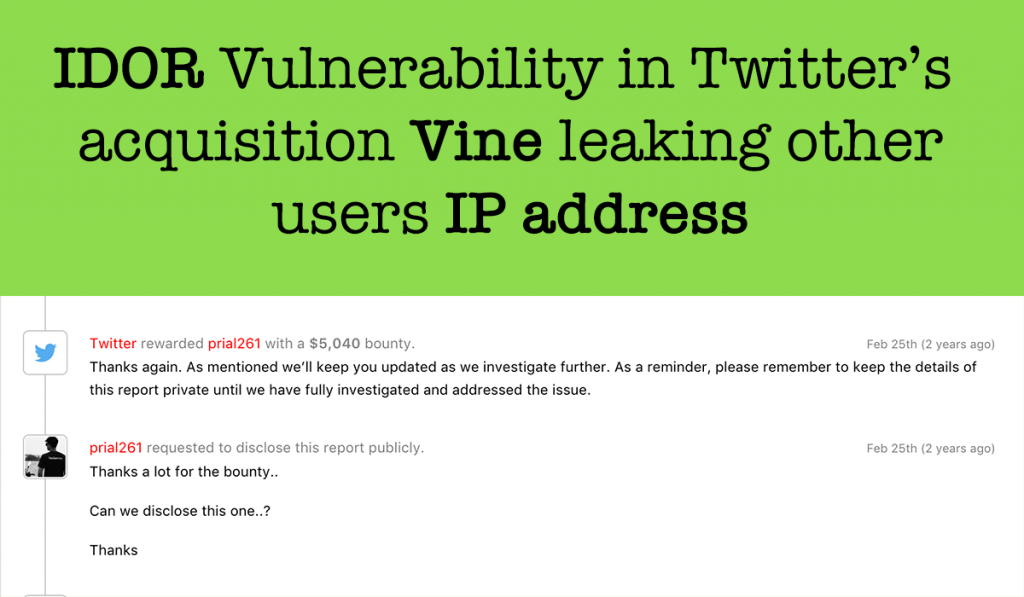
Hi guys, This is one of my old finding adding to my blog. Recently I disclosed a POC on How I was able to get all vine user’s sensitive Information including Phone no/IP Address/Emails and Many more that was reported to Twitter and they patched it and rewarded me 7560$. Those who missed it you […]
Vine User’s Private information disclosure
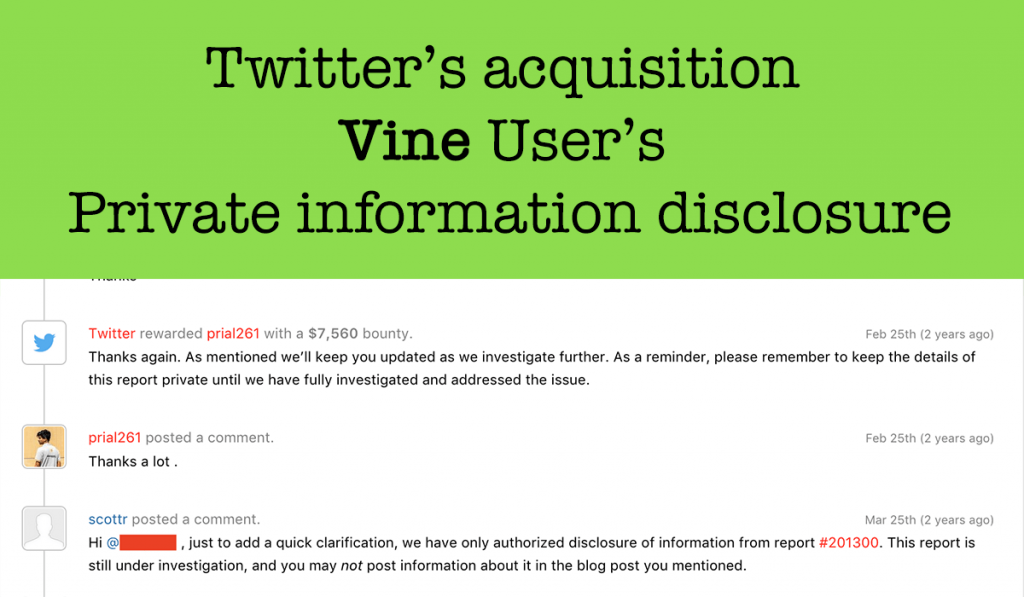
What is Vine? Vine was an American social networking short-form video hosting service where users could share six or seven second-long, looping video clips. It was founded in June 2012; American microblogging website Twitter acquired it in October 2012, well before its official release on January 24, 2013. Today I will write about a Critical […]
Unclaimed Medium Publication takeover in WeTransfer
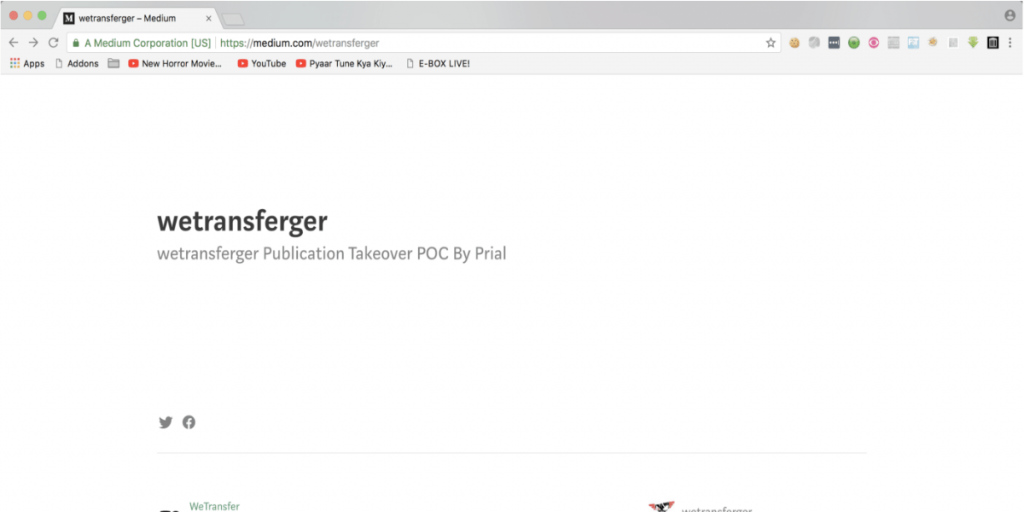
Today I will share a Security issue I found on WeTransfer. WeTransfer has a paid bug-bounty program under Zerocopter. So I start testing their sites. While I was brute-forcing wetransfer.com with DIRB script I got some directories what was redirecting users to the Medium Publication link. Those directories look like https://wetransfer.com/blogger (CODE:301|SIZE:0) (Location: ‘https://medium.com/wetransferger’) https://wetransfer.com/bloggers (CODE:301|SIZE:0) […]
External link warning page bypass in Zerocopter
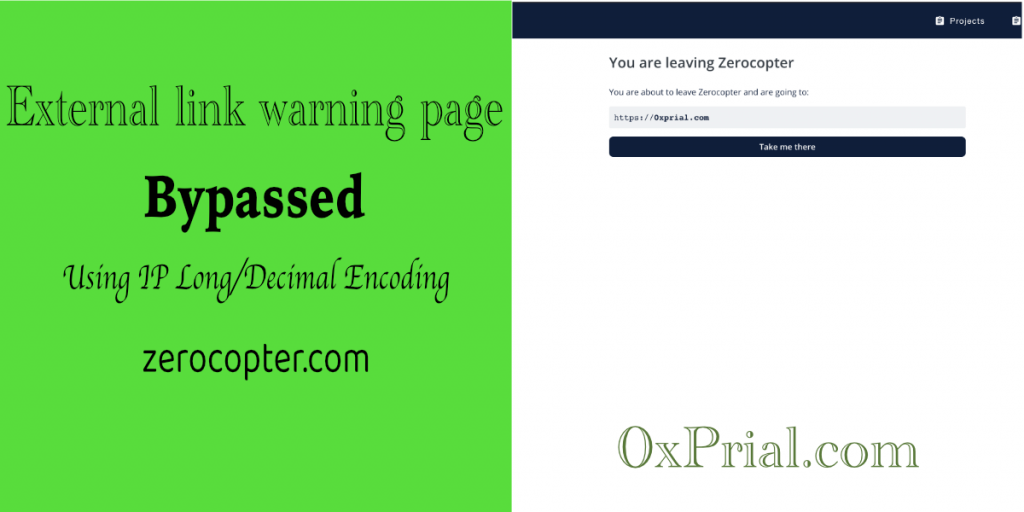
Description: zerocopter.com is a bug bounty platform for Ethical hackers just like Hackerone. In Zerocopter reports, users can use Markdown. Users are also allowed to give external links in reports. If a user clicks on the External link in reports then it takes the user to an external warning page like the below screenshot But I […]
