XSS bypass using META tag in realestate.postnl.nl
Hi readers, Today I will write about a XSS Vulnerability I reported to the postnl.nl bug bounty Program. Reflected XSS A reflected XSS (or also called a non-persistent XSS attack) is a specific type of XSS whose malicious script bounces off of another website to the victim’s browser. It is passed in the query, typically, […]
Unclaimed Medium Publication takeover in WeTransfer
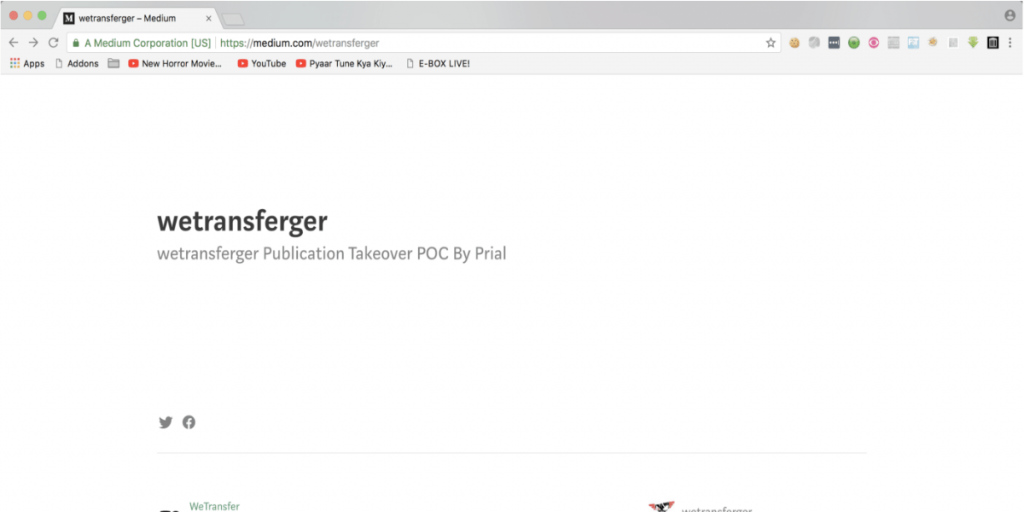
Today I will share a Security issue I found on WeTransfer. WeTransfer has a paid bug-bounty program under Zerocopter. So I start testing their sites. While I was brute-forcing wetransfer.com with DIRB script I got some directories what was redirecting users to the Medium Publication link. Those directories look like https://wetransfer.com/blogger (CODE:301|SIZE:0) (Location: ‘https://medium.com/wetransferger’) https://wetransfer.com/bloggers (CODE:301|SIZE:0) […]
External link warning page bypass in Zerocopter
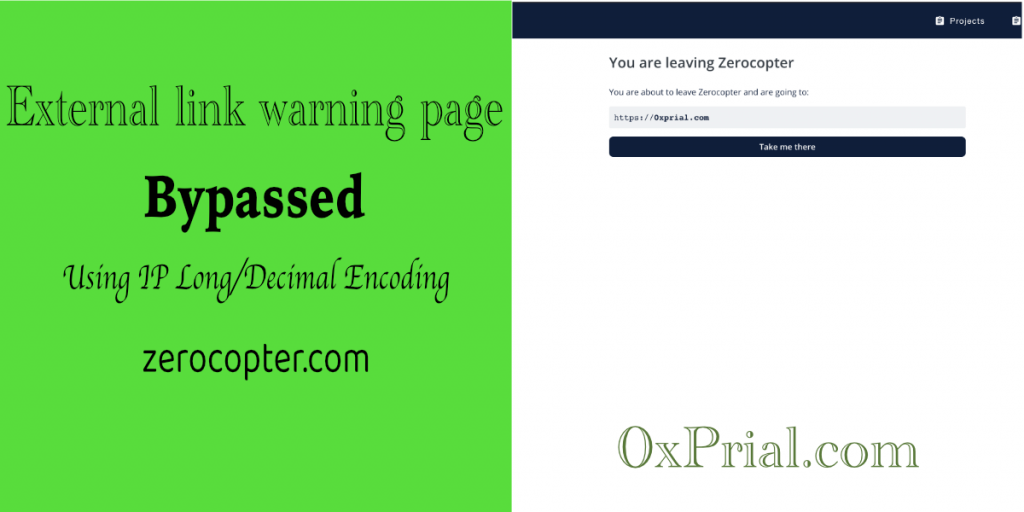
Description: zerocopter.com is a bug bounty platform for Ethical hackers just like Hackerone. In Zerocopter reports, users can use Markdown. Users are also allowed to give external links in reports. If a user clicks on the External link in reports then it takes the user to an external warning page like the below screenshot But I […]
