XSS WAF & Character limitation bypass like a boss
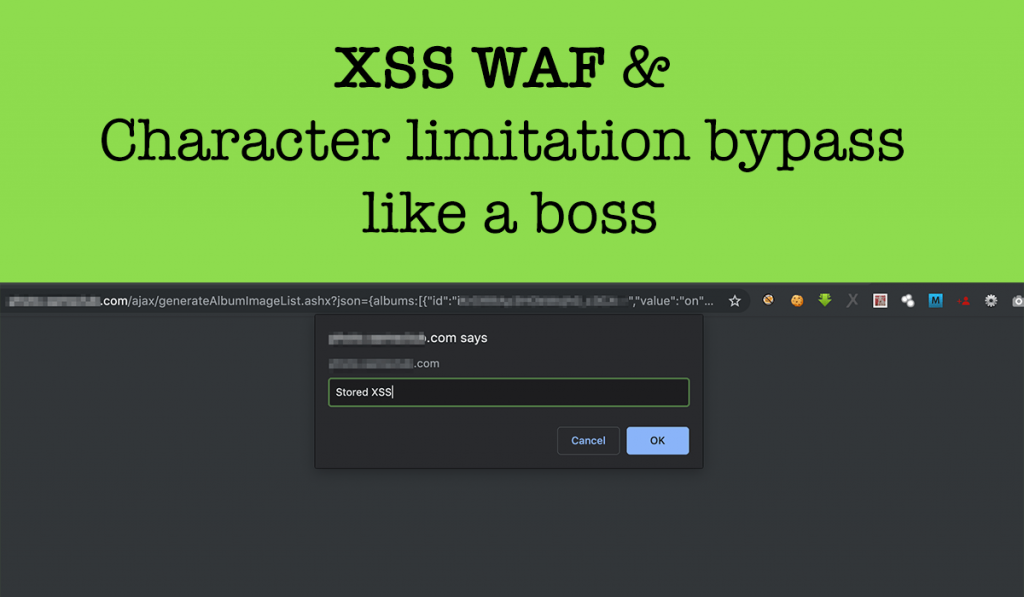
Hello fellow Hackers! I am sitting in my room for the last 3 days due to the coronavirus outbreak worldwide and feeling really bored. So I thought why not do a write-up of what I promised really long ago 🤭. A few months back in My Tweet I shared a way to bypass XSS WAF […]
Unicode vs WAF — XSS WAF Bypass
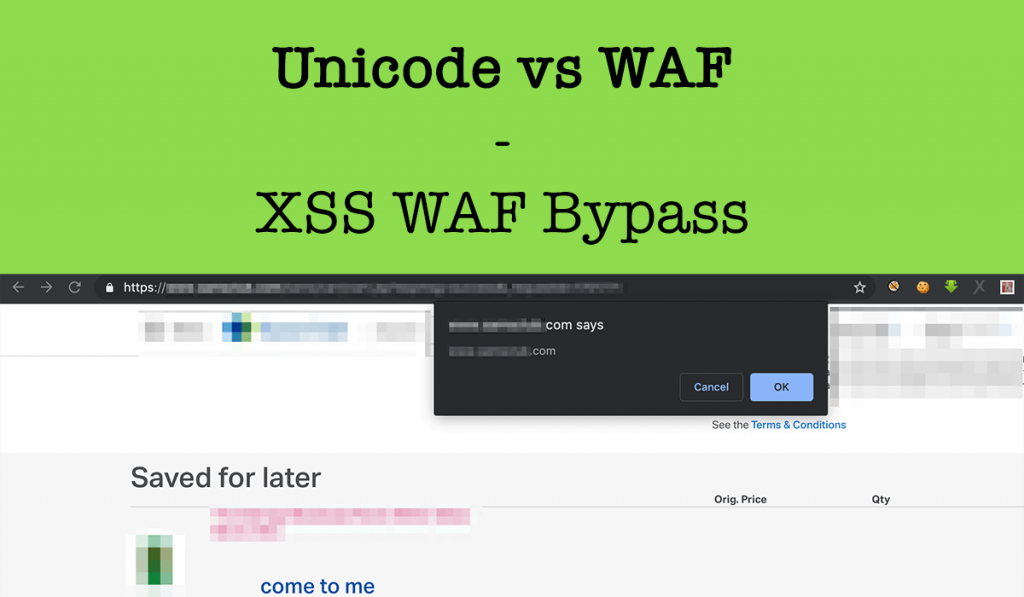
Hi readers, At 1st Eid Mubarak to all. May Allah bring you joy, happiness, peace, and prosperity on this blessed occasion. Wishing you and your family on this happy occasion of Eid! Eid Mubarak! So on this blessed occasion I thought let’s share one of my findings as an Eid bonus 😜 ! From the […]
XSS bypass using META tag in realestate.postnl.nl
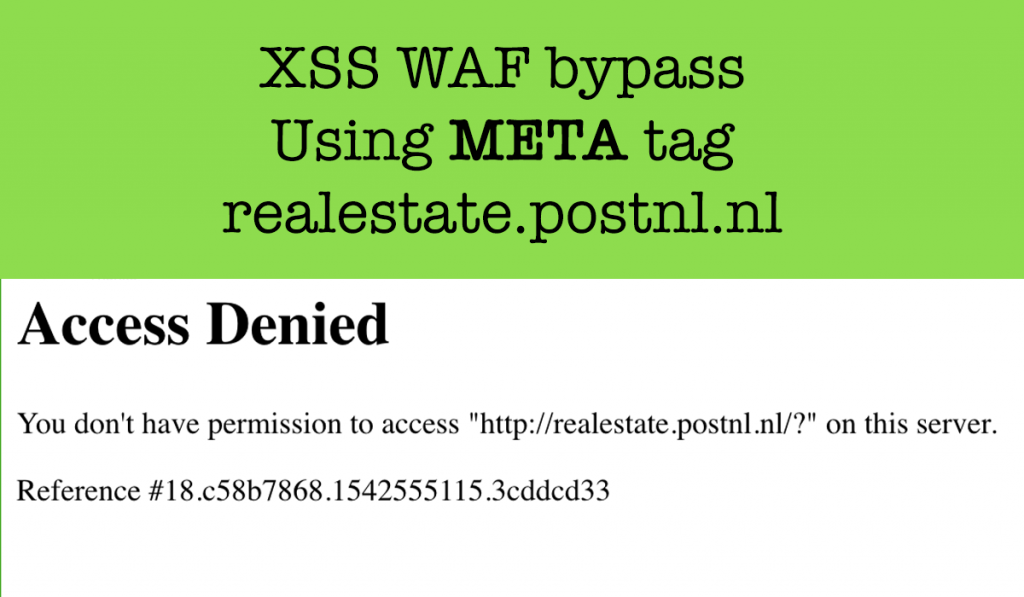
Hi readers, Today I will write about a XSS Vulnerability I reported to the postnl.nl bug bounty Program. Reflected XSS A reflected XSS (or also called a non-persistent XSS attack) is a specific type of XSS whose malicious script bounces off of another website to the victim’s browser. It is passed in the query, typically, […]
