The Art Of Zendesk Hijacking
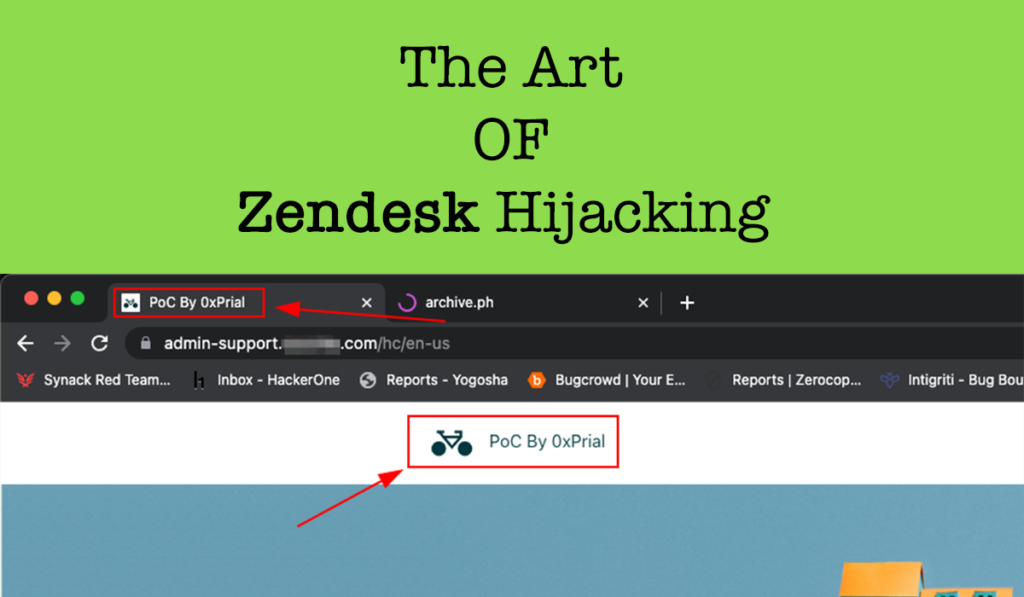
Back in July 2023, I was testing a HackerOne Private Program [ let’s call this target xyz.com ] and this target scope was pretty limited. The scope was – xyz.com admin.xyz.com api.xyz.com The subdomain admin.xyz.com looks interesting and I quickly used search.censys.io to look for any beta or dev environment for this admin subdomain using the query […]
IDOR Leads To Leak Any Uber Eats Restaurant Analytics
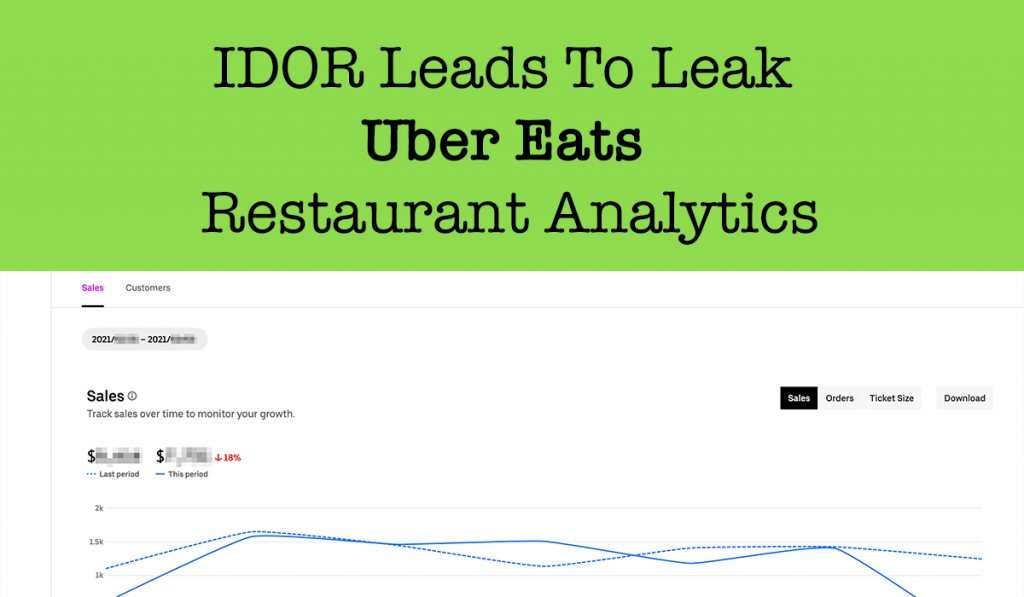
Hi fellow Hackers,At first Ramadan Kareem! Wishing everyone a very happy Ramadan. Today I will write about an Insecure direct object references (IDOR) vulnerability that I recently discovered in Uber Eats Restaurant. The Uber Eats Restaurant web application at https://restaurant.uber.com/ is using GraphQL. Back in March, I was doing a collaboration on a Uber report […]
How I earned 5040$ from Twitter by showing a way to Harvest other users IP address
Hi guys, This is one of my old finding adding to my blog. Recently I disclosed a POC on How I was able to get all vine user’s sensitive Information including Phone no/IP Address/Emails and Many more that was reported to Twitter and they patched it and rewarded me 7560$. Those who missed it you […]
Vine User’s Private information disclosure
What is Vine? Vine was an American social networking short-form video hosting service where users could share six or seven second-long, looping video clips. It was founded in June 2012; American microblogging website Twitter acquired it in October 2012, well before its official release on January 24, 2013. Today I will write about a Critical […]
External link warning page bypass in Zerocopter
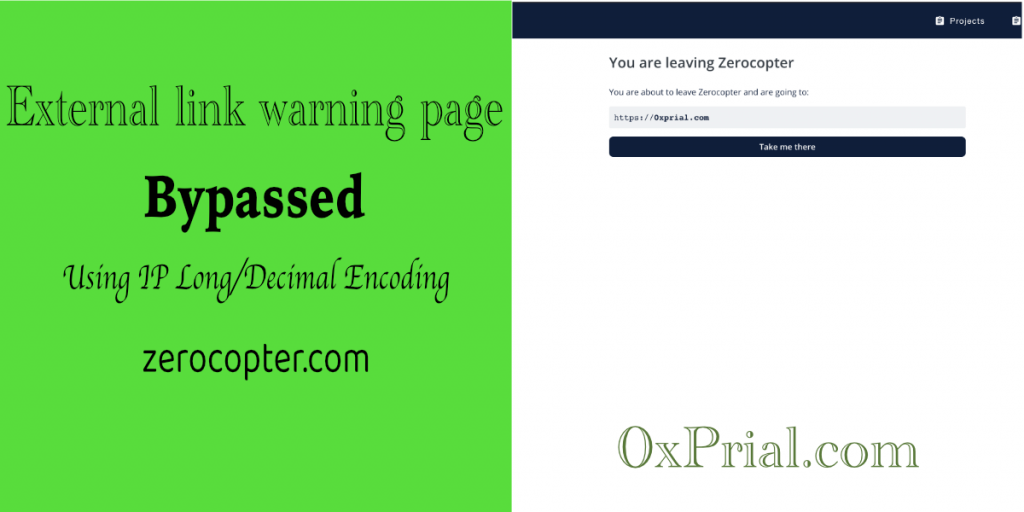
Description: zerocopter.com is a bug bounty platform for Ethical hackers just like Hackerone. In Zerocopter reports, users can use Markdown. Users are also allowed to give external links in reports. If a user clicks on the External link in reports then it takes the user to an external warning page like the below screenshot But I […]
