A common question nowadays is “How to get started in Bug Bounties?” and I keep on getting this message on a day to day basis. It’s not possible for me to respond to each and every message, so I thought I’d rather do a blog post and would direct all those beginners to this blog post.
I am a learner in Hacking Stuff and I’ve been in the bug bounty field for 3+ years now. still, there is so much to learn each and every day, I’m yet not an expert and this post is for mainly those peoples who are an absolute beginner, or someone who is thinking to get started into bug bounty, or someone who is planning to change their field.
What are Bug Bounties?
A bug bounty program is a deal offered by many websites, organizations, and software developers by which individuals can receive recognition and compensation for reporting bugs, especially those pertaining to security exploits and vulnerabilities. These programs allow the developers to discover and resolve bugs before the general public is aware of them, preventing incidents of widespread abuse. Bug bounty programs have been implemented by a large number of organizations, including Facebook, Google, Twitter, Microsoft, Uber, Github, Internet bug bounty, and many more. Companies outside the technology industry, including traditionally conservative organizations like the United States Department of Defense, have started using bug bounty programs hosted on HackerOne.
Formal Education vs Information Security
I’ve seen a lot of guys think someone needs to be from a computer science background to be good in Hacking kinds of stuff. But this is not correct. I am too from a Power Engineering background but I am very much interested in the information security field from school time but joined the Power Engineering field with the advice of family members but my main focus has always been Information security.
Being from a computer science background helps but it is not compulsory but you have to learn the computer science fundamentals yourself. So, If you are from a non-technical background you should get started only if you’re more interested in learning about information security not ONLY interested in $$$.
Keep in mind
- No one will be able to tell you everything about this field, It’s a long path but you have to travel it alone with help from others.
- Do not expect someone will spoon feed you everything.
- Focus less on $ and more on learning.
- If you think you will become successful overnight or over the week or a month, this is not a field you should join.
- Doing bug bounties are very competitive nowadays, it took me more than six months to find my first valid vulnerability, so be patient and practice every day.
Basic Technical things to get started
You must have a basic understanding of how things work on the internet. Learn how things work before getting started into Bug bounty hunting so you don’t have to ask random people why a payload isn’t working. There are many things you have to learn but I cannot list all of them here. I’m listing a few important topics and you should learn more by yourself.
- HTTP/HTTPS: HTTP is a communication protocol that was designed for communication between web browsers and web servers. From this deception, you should understand how important it is. You should go through the below resources to get the basic idea about HTTP Protocols, HTTP Requests, Response, Status Codes, Encoding/Decoding, SOP, Cookie, MIEM & HTML Pharising what will definitely help you later.
-
- https://www.w3schools.com/whatis/whatis_http.asp
- https://www.tutorialspoint.com/http/http_status_codes.htm
- https://www.tutorialspoint.com/http/http_url_encoding.htm
- https://www.tutorialspoint.com/http/http_requests.htm
- https://www.tutorialspoint.com/http/http_responses.htm
- https://www.hacker101.com/sessions/web_in_depth
- Basic Networking: A basic understanding of networking is important for anyone who’s into a computer. I enrolled Certified Network Security Specialist and I personally found it really helpful for me. I can suggest the below resources to learn the basics of Networking.
-
- https://www.wpbeginner.com/glossary/dns/
- https://www.networkworld.com/article/3268449/what-is-dns-and-how-does-it-work.html
- https://www.cloudflare.com/learning/dns/what-is-dns/
- https://www.icsi.co.uk/courses/icsi-cnss-certified-network-security-specialist-covid-19
- https://www.geeksforgeeks.org/tcp-ip-model/
- https://www.youtube.com/watch?v=0AcpUwnc12E&list=PLkW9FMxqUvyZaSQNQslneeODER3bJCb2K
- https://commotionwireless.net/docs/cck/networking/learn-networking-basics/
- https://www.slideshare.net/variwalia/basic-to-advanced-networking-tutorials
- https://www.utilizewindows.com/list-of-common-network-port-numbers/
- https://www.digitalocean.com/community/tutorials/an-introduction-to-networking-terminology-interfaces-and-protocols
- Linux Commands: You should have knowledge of Linux OS commands.
- Programming/Coding: To be a Good Hacker you don’t really need to be a Good Programmer but it’s always good to cover the basic level so that you understand what’s happening there after looking at a chunk of codes. If you understand the code Sometimes It increases your chances of successfully identifying and exploiting a vulnerability and also you may need code to escalate a bug with a low/medium severity to high/critical. Back in 2016 when I was just learning XSS vulnerability and I don’t have good knowledge of programming and all I used to do is just copy-paste XSS payloads in user inputs without understanding a thing and the fun fact is I used to test with below payloads without understanding that all those were the same and I was just wasting my time 😷
<img src=x onerror="alert(document.domain)"> <IMG SRC=A onerror="alert(document.domain)"> <IMG SRC=B onerror="alert(document.domain)"> <IMG SRC=b onerror="alert(document.domain)"> <IMG SRC=# onerror="alert(document.domain)"> <IMG SRC=x onerror="alert(document.domain)"> <IMG SRC=y onerror="alert(document.domain)"> <IMG SRC=Z onerror="alert(document.domain)">
After reading my story hope you guys understand how basic knowledge in coding can save your time and give you more advantages in the future with automation and exploration. I’ll suggest a few languages that one should properly have basic to medium level knowledge about and keep advancing it.
HTML :
- https://www.w3schools.com/html/
- https://www.codecademy.com/learn/learn-html
- https://htmldog.com/guides/html/advanced/
PHP :
- https://www.w3schools.com/php/
- https://www.codecademy.com/learn/learn-php
- https://www.guru99.com/php-tutorials.html
- https://www.codecademy.com/learn/paths/web-development
JavaScript :
- https://www.w3schools.com/js/
- https://www.youtube.com/watch?v=PkZNo7MFNFg
- https://www.codecademy.com/learn/introduction-to-javascript
SQL(Structured Query Language) :
- https://www.youtube.com/watch?v=HXV3zeQKqGY
- https://www.w3schools.com/sql/
- https://www.codecademy.com/learn/learn-sql
Automation: "Never send a human to do a machine’s job". Knowledge in the below languages will help you to automate your tasks easily. Knowledge in these languages will help you to code your own tools and understand many other common tools and modify them according to your needs.
Bash :
- https://0xprial.com/wp-content/uploads/2021/02/bash-bug-bounty.pdf
- https://0xprial.com/wp-content/uploads/2021/02/Coding-For-Pentester.pdf
- https://www.tutorialspoint.com/unix/shell_scripting.htm
- https://www.learnshell.org/
- https://medium.com/quick-code/top-tutorials-to-learn-shell-scripting-on-linux-platform-c250f375e0e5
Ruby :
Python :
- https://realpython.com/
- https://www.amazon.com/Python-Web-Penetration-Testing-Cookbook-ebook/dp/B00YSILC2K
- https://docs.python.org/3/tutorial/
- https://www.pcwdld.com/python-cheat-sheet
Golang :
- https://tour.golang.org/welcome/1
- https://www.udemy.com/learn-go-the-complete-bootcamp-course-golang/
Chose a Path to learn
Now it’s time to learn about vulnerabilities. In a Bug Bounty program, you may encounter different types of assets testing like
- Source Code
- IoT
- Hardware
- Reverse Engineering
- Host
- Mobile Application
- Web Application
You have to choose one of them to start learning. Most of the guys choose the Web application asset first because it’s the easiest one.
Learning about Vulnerabilities
One vulnerability at a time. Look at OWASP’s Top 10 vulnerabilities and pick one vulnerability then master it. Create your own local sandbox environment and test for that type of vulnerability. Play with the application and try to find out why it is vulnerable. Then look for it everywhere on the internet [Test with proper permission or responsible disclosure policy]. While learning for a vulnerability keep the below points in mind
- How to test for that vulnerability and identify it?
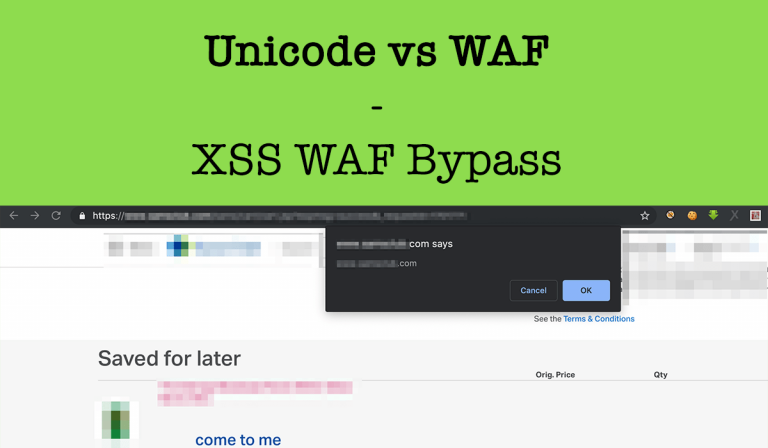
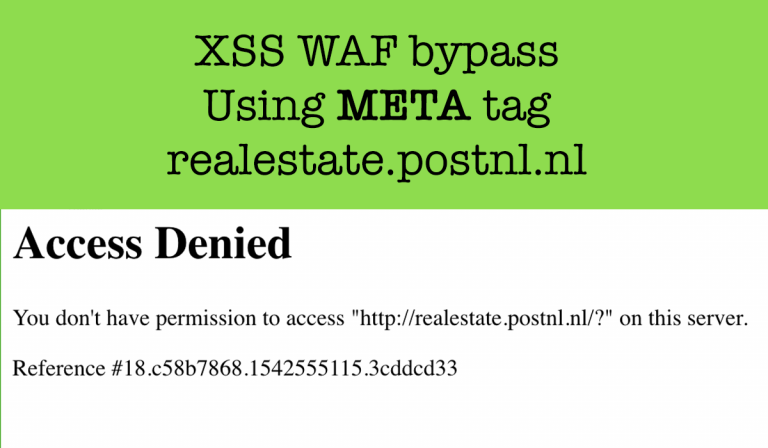
- How to bypass WAF and other common defenses?
- How a fixed/secured application endpoint looks or reacts like?
Let’s me show you guys my way of learning new things, let’s start with XSS vulnerabilities. Whenever I try to learn new things in infosec I first ask google as “Google is your friend”. So I will just search using the below dorks and open all results in new tabs and read them all and try to figure out how those were discovered and how those vulnerabilities were tested.
- XSS site:hackerone.com
- XSS site:medium.com
- XSS POC site:youtube.com
Then I will test what I learned on my localhost. I was able to find below codes that I used when I was practicing XSS back in 2016.
<?php
$val=htmlspecialchars($_GET['no_xss'],ENT_QUOTES);
$val2=$_GET['xss'];
$val3=htmlspecialchars($_GET['r_xss'],ENT_QUOTES);
?>
<html>
<body>
<center>
<h1>
Injection Point 1 :- <?=$val2?><br>
Injection Point 2 :- <?=$val?><br>
<a href="<?=$val3?>">Tricky XSS :')</a>
</h1>
</center>
</body>
</html>
There are many other vulnerable apps available. You can use them to gain practical experience on a vulnerability. Some of them are:
CTFs are not always great for learning:
- Real targets are never going to be as vulnerable as a CTF is.
- The more you rely on learning from them the harder the jump is to real targets.
- Although the experience will help you in Bug Bounty but the transition is never going to be easy.
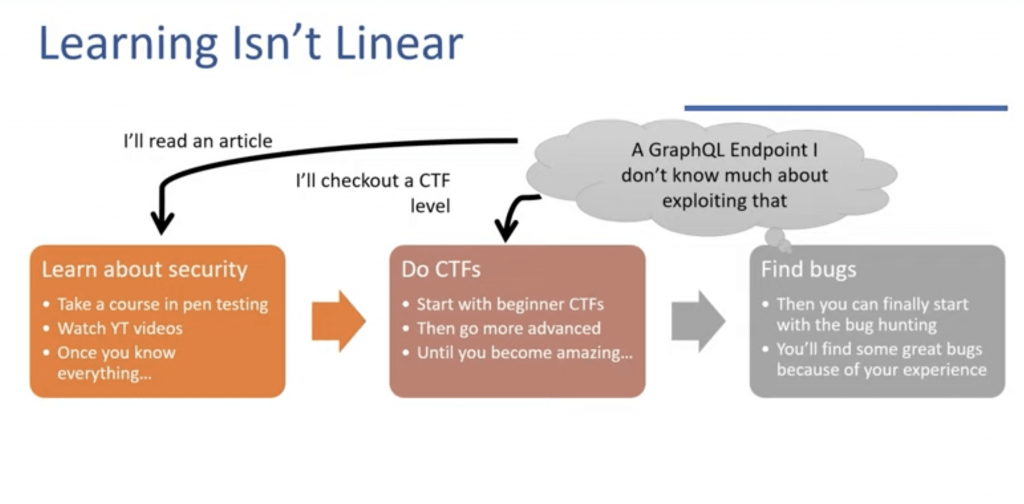
Learning new stuff while testing:
While you are testing for a specific vulnerability type you may encounter something fishy. For example, you discover a graphQL endpoint but you don’t know much about that. So would you ignore that? No! note that endpoint, stop testing then
- Go to google and learn about that technology and then came back to that endpoint to test for vulnerabilities.
- If that didn’t work setup that technology or application in sandbox and test there for gaining experience.
Read other Researchers write-ups and disclosed reports
Regularly read other researcher’s writeups to understand their methodology and learn about how they approach vulnerabilities. I will suggest starting with InfoSec Write-ups what contains a huge amount of POC write-ups for many researchers. Also regularly keep eye on Hackerone’s Hacktivity. Reading other researchers write-ups and Hackerone disclosed reports allows you to
- Learn about other hackers thinking and what they found.
- Understand other researchers thinking and testing process.
- How they are approaching a vulnerability.
- How they tested for that vulnerability.
Reconnaissance
Recon is a set of processes and techniques (Footprinting, Scanning & Enumeration) used to covertly discover and collect information about a target system. During reconnaissance, an Ethical Hacker attempts to gather as much information about a target system as possible. For recon, I will suggest reading Dirty-Recon.pdf
Should you rely on automated tools?
As a beginner, you should avoid automated tools unless you know what and how that tool is working,
- Don’t rely on tools, except for a proxy.
- Use tools only when you understand how and why they work.
Which targets should you choose as a beginner?
As a beginner, you should avoid the bounty program and give those efforts to VDP programs to earn reputation points, Hall Of Fames, and swags. You will also earn experience with it. Focus less on $$$ and more on learning, test programs with VDP, or independent sites that offer Hall Of Fame or Swags. There are lots of queries you could search for such a program on google, however here are some popular search queries: (don’t forget to try different languages!)
inurl:responsible disclosure inurl:security site:target.com "report security vulnerability" "vulnerability disclosure" "powered by hackerone" "submit vulnerability report" indesc:bug bounty|vulnerability disclosure inurl: bug bounty white hat program "vulnerability reporting policy" inurl:responsible-disclosure-policy
Pick a program you love and hunt there for a long time.
Writing a Decent Vulnerability Report
In BugBounty Writing a well-explained Report is the most important part. If you don’t write a good and well-described report you may end up making confusion with the Triage team, what could result –
- Less Payment than expected.
- Report closed as N/A.
- Will take more time to confirm the vulnerability by the Triage team.
On the other hand, if your report is well explained / clear and contains all the info then it will take less time to confirm the vulnerability and you will get your reward soon. Even you may get Bonus rewards for your creative and detailed report. I got many such rewards where that report should be closed as Won’t Fix or Out Of Scope. See a few example scenario below –
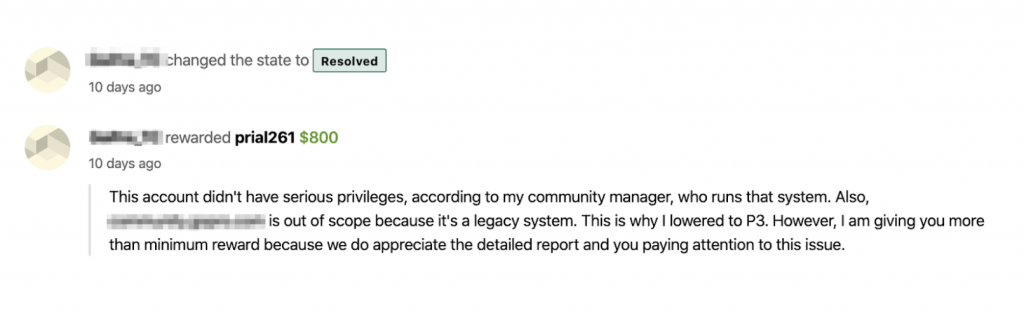
Scenario 1: In the below screenshot it was a vulnerability in Out Of Scope asset, but I showed them how it can lead to a good impact attack by writing a detailed report and they rewarded me $800 and appreciated my detailed report.
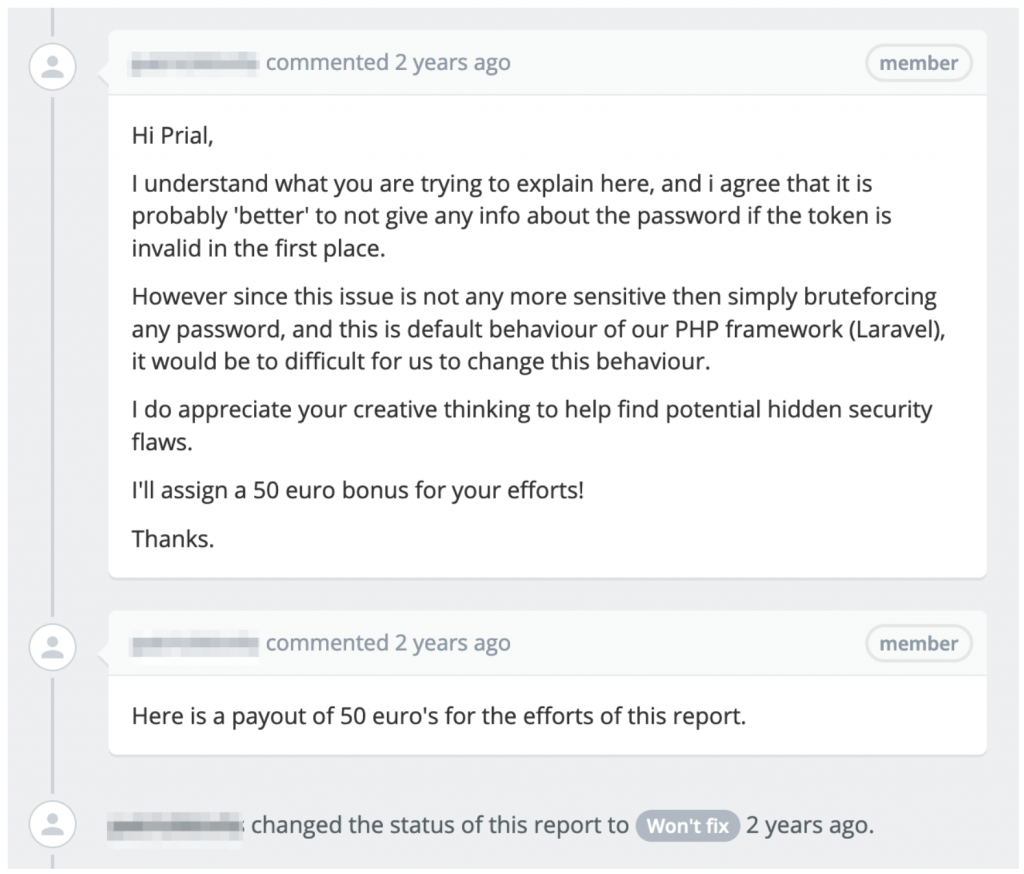
Scenario 2: In the below screenshot the company was an online Banking service and the vulnerability was using an expired/used password reset token of a user attacker can brute-force for login password which could lead to account takeover. But it was a vulnerability of the PHP framework and according to the policy, it will go under Not Accepted vulnerability. But for my detailed report, they paid a €50 bonus for a report what was Closed as Won’t fix.
From the Above Scenarios, you should understand that how much important it is to write a detailed and well-explained report. A vulnerability report should contain the below contents:
- Title
- Summary
- Description
- Vulnerable Endpoint
- How You discovered it
- How to reproduce
- Impact & Scenario
- Recommended Fix
Title: In a vulnerability title you have to give a title about the vulnerability you are going to report. For example, you discovered a Reflected XSS in the 0xPrial.com domain’s contact endpoint. So the title will be something like: Reflected XSS in 0xPrial.com domain’s contact endpoint.
Summary: In this section give a short summary of the vulnerability.
Description: In description give detailed information about the vulnerability. For example, if you are reporting an XSS in the contact form then describe how XSS is happening on that endpoint and how it’s working.
Vulnerable Endpoint: List down all the URLs/endpoints/assets that are vulnerable to that security issue.
How You discovered it: In this section describe how you discovered that endpoint and vulnerability, list all scripts or tools you used to do it here.
How to reproduce: This is the most important part of a report. In this step write down all the necessary steps to reproduce the issue you discovered step by step. So-that triage team can follow it and reproduce the issue. It will be easy to follow your steps by the triage team if you add screenshots with every step. Also, you can create a video POC and add it to your report.
Impact & Scenario: Your bounty reward amount mostly depend on this section. In this section, you have to explain how an attacker can use that vulnerability to do something malicious against that organization. Describe what is the impact of your discovered vulnerability. What else you can do with this vulnerability, What an attacker can achieve using this vulnerability, How an attacker can attack another user using this etc. Also, add a real-life attack scenario in this section if possible to make the report more impactful.
Recommended Fix: Suggest a fix for that vulnerability. Dev team will push a fix according to suggestions and will ask you to retest again the fix.
Always keep the below points in mind while writing a report :
- Never upload your POC screenshot/Video to a place where everyone can see it. But You can use youtube to upload your POC video but ask about uploading it to youtube from that organization’s security team + upload it as an Unlisted Video.
- Never publicly disclose your report or vulnerability details before it’s fixed properly.
- Before publicly disclosing a vulnerability take permission from the company.
- If possible Use a public PGP key to encrypt your message while reporting.
Some write-ups on writing a quality report
- Writing Successful bug Submissions Bug Bounty hunter methodology
- Writing a good and detailed vulnerability report
- What does a good report look like?
Must read
- Web Hacking 101 [ Get a free copy from https://hackerone.com/resources/web-hacking-101 ]
- Resources for Beginner Bug Bounty Hunters
- Web Application Hacker’s Handbook
- Mastering Modern Web Penetration Testing
- The Hacker Playbook 1, 2 and 3
- The Mobile Application Hacker’s Handbook
- Breaking into Information Security
Twitter # tag you should follow
Blogs You should follow
There are plenty of blogs Shared by Hackers daily that you can read to learn more and more. [ Any Blog Link Missing? Kindly add it in Comments ]
- http://www.shawarkhan.com/
- https://blog.securitybreached.org/
- https://blog.detectify.com/
- http://geekboy.ninja/
- http://bugbountypoc.com/
- https://www.hackerone.com/blog
- https://forum.bugcrowd.com/
- https://securitywall.co/
- https://0xpatrik.com/
- https://blog.it-securityguard.com/
- https://blog.innerht.ml/
- http://brutelogic.com.br/blog/
- https://seanmelia.wordpress.com/
- https://respectxss.blogspot.com/
- https://www.gracefulsecurity.com/
- https://whitton.io/
- https://tisiphone.net/
- http://archive.nahamsec.com/
- https://www.hackerscreed.org/
- http://danlec.com/blog
- https://wehackpeople.tumblr.com/
- https://bitquark.co.uk/blog/
- https://www.arneswinnen.net/
- https://medium.com/@arbazhussain/
- http://www.rafayhackingarticles.net/…
- http://www.securitytube.net/
- https://hackasia.org/
- http://www.gangte.net/
- https://mukarramkhalid.com/
- https://securitytraning.com/
- https://jubaeralnaziwhitehat.wordpress.com/
- http://www.securityfocus.com/
- http://www.blackhat.com/
- https://www.metasploit.com/
- http://sectools.org/
- https://labs.detectify.com/
- https://blog.rubidus.com/
- http://www.securityidiots.com/
- https://hackernoon.com/
- https://sqli-basic.blogspot.com/
- https://bugbaba.blogspot.in/
- https://vulnerability-lab.com/
- https://medium.com/@know.0nix/
- https://medium.com/@codingkarma/
YouTube Channels You should follow.
These Channels are Shared By Hackers where They Upload their Video POC’s. Watching them you can understand how to demonstrate these types of attacks. [ Any Channel Link Missing? Kindly add it in Comments ]
- Nahamsec
- coding
- securityidiots.com
- Black Hat
- Shawar Khan
- Hacking Simplified
- Saad Ahmed
- Hisham Mir
- Devil Killer
- Girish Kumar
- Muhammad Khizer Javed
- Suleman Malik
- madrobot
- Harsh Jaiswal
- Frans Rosén
- HackerOne
- Bugcrowd
- josue Fernandez
- vulnerability0lab
- Vijay Kumar
- Mohamed Niyaaz
- Web Development Tutorials
- Jan Wikholm
- Bhargav Tandel
- ErrOr SquaD
- Arbin Godar
- Ameer Assadi
- Penetration Testing in Linux
- Behroz Alam
- Behroz Alam
- Farah Hawa
- 0xPrial 😜
At last pro tips for asking questions
asking good questions pic.twitter.com/nRKvVHaRQM
— 🔎Julia Evans🔍 (@b0rk) December 31, 2016
Thanks for reading. Is there anything I missed? Feel free to let me know on the comment or contact me on Facebook.


162 Responses
It was great
Just awesome Bhai. As a newbie in this field, I was just looking for this type of article. Just love it 😍 . Hope it will help me to grow my skill. Waiting for the next part.
Great, happy to hear you 😀
awshome
Thanks for such a clean and helpful post.
it really helped a lot . Dhonnobaad bhai
Happy to hear your feedback 😇
Thank You sooo soooooooooooooooo Much..!!
Happy to hear your feedback 😇
A great and awesome write-up for newbie and begginer like me. It will help so much for learning in this field.
Thanks for the write-up Lombu.
Happy to hear your feedback 😇
Waiting for part-2 🙂
Alhamdulillah, finay i found it❤️
Thanks to Almighty Allah.
Dear, respectable mentor vaiya keep always supporting us😍
Vaiya, Many Bounty program only use Paypal for Payment Gateway. But As Bangladeshi citizen, Paypal is not available for us. What should we do? How can we use Paypal? Any guidelines will be highly appreciated
You can ping me at twitter @0xPrial to talk about this!
Nice informative article brother! 👌👌
Thanks 😀
I am looking for this type of blog. It’s very very helpful to me. Thanks a lot brother, and we wanna see your cyber security journey in the next blog.
Sure, I will try to write on it 😀
Vai ai part gulo banglai korle aktu valo hoto.
Bug Bounty and Hacking needs good communication skill as well. Also this article was meant for all.
Is it just me or this blog is a lot similar to javed bhai’s blog . Nice one and informative one. Just wanted to point that out.
Yes, you should feel it in some points as I also read his one and his resources were really cool so why not use those. Also, I have written my blog from my point of view and experiences. You should see differences between 2 blogs.
Ma Shaa Allah!
It’s a very informative blog bhaiya🤍.
Waiting for 2nd part 🤍
Keep in touch <3
OMG! this is really a very helpfull..
Keep in touch and do share this on social. 😀
Very informative and helpful blog brother. We want more blog such as like this one!
Awsome dude 😍
Hello great website! Does running a blog similar to this require a lot of work?
I have very little understanding of coding however I was hoping to start my own blog in the near
future. Anyhow, if you have any ideas or tips for new blog owners please share.
I understand this is off topic however I just had to ask.
Thank you!
Hi there,
I do blog writeups whenever I get the time and do writeups on my findings during my research on the web and mobile applications. If you have skill in any field then you can start writing on that topic and others will grab your articles to know more.
Thanks.
Does your blog have a contact page? I’m having a tough time locating it but, I’d like to shoot you an e-mail.
I’ve got some creative ideas for your blog you might be interested in hearing.
Either way, great website and I look forward to seeing it expand over time.
Yes, You can contact me from https://0xprial.com/contact/ or just email me in**@*ri.al 😀
Do you mind if I quote a couple of your posts as long as I provide credit and sources back to your webpage?
My blog site is in the exact same niche as yours and my visitors would really benefit from
a lot of the information you present here. Please let me know if this ok with you.
Regards!
Sure thing, you can share on your blog. Comment out your post link here too 😀
Excellent items from you, man. I have bear in mind your stuff
prior to and you’re simply extremely great. I really like what you’ve acquired right here,
certainly like what you are saying and the way in which during
which you say it. You are making it entertaining and
you still care for to stay it wise. I can not wait to learn far more from you.
This is really a terrific website.
Thanks 😀
Such texture, many shade, so admirable
Thanks for your feedback
Hello, Neat post. There is an issue along with your website in web explorer, would test this?K IE nonetheless is the marketplace leader and a good portion of folks will pass over your great writing due to this problem.
Thanks for your feedback
I am sure this paragraph has touched all the internet people, its really really fastidious paragraph on building up new website. Robert Cecilio
Thanks a lot for your feedback 😀
I constantly emailed this webpage post page to all my associates, for the reason that if like to read it next my links will too. Kendall Mountjoy
Thanks a lot for your feedback 😀
Pretty section of content. I just stumbled upon your weblog and in accession capital to assert that I acquire actually enjoyed account your blog posts. Anyway I will be subscribing to your feeds and even I achievement you access consistently rapidly.
Thanks a lot for your feedback 😀
I’d must check with you here. Which is not one thing I normally do! I take pleasure in studying a submit that will make folks think. Also, thanks for permitting me to comment!
Thanks a lot for your feedback 😀
Hurrah! Finally I got a weblog from where I be capable of in fact get helpful information concerning my
study and knowledge.
Thanks a lot for your feedback 😀
I’m not sure exactly why but this blog is loading extremely slow for me.
Is anyone else having this issue or is it a issue on my end?
I’ll check back later and see if the problem still exists.
Site was under development at that time. Can you check now and give me update if the issue still exists?
I appreciate you sharing this blog post. Thanks Again. Cool.
Thanks a lot for your feedback 😀
I do not even understand how I ended up here, but I assumed this publish used to be great
Will continue publishing new contents soon 😀
Awesome! Its genuinely remarkable post, I have got much clear idea regarding from this post
Thanks a lot for your feedback 😀
Good post! We will be linking to this particularly great post on our site. Keep up the great writing
Thanks a lot for your feedback 😀
I am truly thankful to the owner of this web site who has shared this fantastic piece of writing at at this place.
Thanks a lot for your feedback 😀
I will immediately seize your rss as I can not to find your email subscription linkor newsletter service. Do you’ve any? Kindly let me recognize in order that I may just subscribe.Thanks.
There is a Newsletter available at bottom of the site https://0xprial.com/ where you can subscribe.
very informative articles or reviews at this time.
I truly appreciate your technique of writing a blog. I added it to my bookmark site list and will
Thanks a lot for your feedback <3
Good post! We will be linking to this particularly great post on our site. Keep up the great writing
Thanks a lot for your feedback <3
Hi there to all, for the reason that I am genuinely keen of reading this website’s post to be updated on a regular basis. It carries pleasant stuff.
Thanks a lot for your feedback <3
You’re so awesome! I don’t believe I have read a single thing like that before. So great to find someone with some original thoughts on this topic. Really.. thank you for starting this up. This website is something that is needed on the internet, someone with a little originality!
Thanks a lot for your feedback <3
This is really interesting, You’re a very skilled blogger. I’ve joined your feed and look forward to seeking more of your magnificent post. Also, I’ve shared your site in my social networks!
Great 😀 , Thanks a lot for your feedback <3
I’m often to blogging and i really appreciate your content. The article has actually peaks my interest. I’m going to bookmark your web site and maintain checking for brand spanking new information.
Thanks a lot for your feedback <3
I truly appreciate your technique of writing a blog. I added it to my bookmark site list and will
Thanks a lot for your feedback <3
very informative articles or reviews at this time.
Thanks a lot for your feedback <3
very informative articles or reviews at this time.
Thanks a lot for your feedback <3
I truly appreciate your technique of writing a blog. I added it to my bookmark site list and will
Thanks a lot for your feedback <3
Hi there to all, for the reason that I am genuinely keen of reading this website’s post to be updated on a regular basis. It carries pleasant stuff.
Thanks a lot for your feedback <3
There is definately a lot to find out about this subject. I like all the points you made
Thanks a lot for your feedback <3
I like the efforts you have put in this, regards for all the great content.
Thanks a lot for your feedback <3
I really like reading through a post that can make men and women think. Also, thank you for allowing me to comment!
Nice post. I learn something totally new and challenging on websites
You’re so awesome! I don’t believe I have read a single thing like that before. So great to find someone with some original thoughts on this topic. Really.. thank you for starting this up. This website is something that is needed on the internet, someone with a little originality!
Thanks for your precious words 😀
I do not even understand how I ended up here, but I assumed this publish used to be great
Nice post. I learn something totally new and challenging on websites
Thanks for your precious words 😀
I like the efforts you have put in this, regards for all the great content.
Thanks for your precious words 😀
I’m often to blogging and i really appreciate your content. The article has actually peaks my interest. I’m going to bookmark your web site and maintain checking for brand spanking new information.
Thanks for your precious words 😀
Very well presented. Every quote was awesome and thanks for sharing the content. Keep sharing and keep motivating others.
Thanks for your precious words 😀
Pretty! This has been a really wonderful post. Many thanks for providing these details.
Thanks for your precious words 😀
Awesome! Its genuinely remarkable post, I have got much clear idea regarding from this post
Thanks for your precious words 😀
I just like the helpful information you provide in your articles
Thanks for your precious words 😀
Ataşehir Web Tasarım Firması, Web Tasarım İnternet Sitesi Tasarımı http://www.webdesin.net İstanbul Ataşehir Türkiye Web Tasarım
gerçekten çok yararlı bi konu teşekkürler
Thanks for your precious words 😀
This was beautiful Admin. Thank you for your reflections.
Thanks for your precious words 😀
I truly appreciate your technique of writing a blog. I added it to my bookmark site list and will
Thanks for your precious words 😀
There is definately a lot to find out about this subject. I like all the points you made
I do not even understand how I ended up here, but I assumed this publish used to be great
Fantastic blog. Really looking forward to read more. Keep writing. Wendell Balmes
Thanks for your precious words 😀
I really like your writing style, wonderful information, appreciate it for posting : D. Daryl Klaren
Thanks for your precious words 😀
This is my first time pay a quick visit at here and i am really happy to read everthing at one place
Thanks for your precious words 😀
Hiya! Quick question that’s completely off topic. Do you know how
to make your site mobile friendly? My web site looks weird
when browsing from my iphone 4. I’m trying to find a
theme or plugin that might be able to resolve this issue.
If you have any recommendations, please share. Thanks!
You should contact any web developer on this matter I guess 😀
This is a topic which is close to my heart… Take care! Exactly
where are your contact details though?
Great, Thanks for your words 😀
You can contact me from https://0xprial.com/contact/ or in**@*ri.al
I just like the helpful information you provide in your articles
Great, Thanks for your words 😀
Pretty! This has been a really wonderful post. Many thanks for providing these details.
Great, Thanks for your words 😀
I appreciate you sharing this blog post. Thanks Again. Cool.
Great, Thanks for your words 😀
Awesome! Its genuinely remarkable post, I have got much clear idea regarding from this post
Great, Thanks for your words 😀
There is definately a lot to find out about this subject. I like all the points you made
This is really interesting, You’re a very skilled blogger. I’ve joined your feed and look forward to seeking more of your magnificent post. Also, I’ve shared your site in my social networks!
Great, Thanks for your words 😀
This is my first time pay a quick visit at here and i am really happy to read everthing at one place
Thanks for your words 😀
Nice post. I learn something totally new and challenging on websites
Thanks for your words 😀
I’m often to blogging and i really appreciate your content. The article has actually peaks my interest. I’m going to bookmark your web site and maintain checking for brand spanking new information.
For the reason that the admin of this site is working, no uncertainty very quickly it will be renowned, due to its quality contents.
I am truly thankful to the owner of this web site who has shared this fantastic piece of writing at at this place.
Nice post. I learn something totally new and challenging on websites
I truly appreciate your technique of writing a blog. I added it to my bookmark site list and will
I appreciate you sharing this blog post. Thanks Again. Cool.
I appreciate you sharing this blog post. Thanks Again. Cool.
I truly appreciate your technique of writing a blog. I added it to my bookmark site list and will
I do not even understand how I ended up here, but I assumed this publish used to be great
very informative articles or reviews at this time.
Hi there to all, for the reason that I am genuinely keen of reading this website’s post to be updated on a regular basis. It carries pleasant stuff.
This was beautiful Admin. Thank you for your reflections.
Good post! We will be linking to this particularly great post on our site. Keep up the great writing
Pretty! This has been a really wonderful post. Many thanks for providing these details.
hello brother i just learn bug bounty
plz help me
This site definitely has all of the information I needed about this subject
Thanks for sharing your info. I truly appreciate
your eforts and I will be waiting for your next write ups thanks once again.